Tag: Microsoft
The 5 most common types of Cyber attacks in 2022
Increasingly cybersecurity needs to be thought of as a critical component in business continuity. It is the beating heart of business, how we communicate and collaborate. Failure in this critical component can bring business to a grinding halt. This article will cover:
- Cyber security statistics
- 5 most common types of Cyberattacks
- Security best practices
- Microsoft Security Solutions

With ever increasingly complex environments, with hybrid work and the move to the cloud, the risk only increases.
Let’s look at some statistics to put this into context:
- 2021 was one of the most active years for cyberattacks. According to Check Point Research, cyberattacks increased 50% year-over-year, with each organization facing 925 cyberattacks per week globally.
- The average total cost of a data breach increased from $3.86 million to $4.24 million in 2021. (IBM)
- In 2020, the average time to identify a breach was 207 days. (IBM)
- 95% of cybersecurity breaches are a result of human error (Cyberint)
- The five most common cyberattacks in 2021 included phishing, ransomware, malware, data breach and Distributed Denial of Service DDoS
The 5 most common types of cyber-attack:
1: Phishing:
Phishing is a type of social engineering that uses emails, text messages, or voice mails that appear to be from a reputable source to convince people to give up sensitive information or click on an unfamiliar link. Phishing and other types of social engineering attacks are the most prevalent and dangerous types of cyberattacks. 85% of breaches involve the human element (Verizon). Phishing attacks are responsible for more than 80% of reported security incidents, with 90% of data breaches occur due to phishing (Cisco).
2: Ransomware:
Ransomware is a form of extortion that uses malware to encrypt files, making them inaccessible. Attackers often extract data during a ransomware attack and may threaten to publish it if they don’t receive payment. In exchange for a decryption key, victims must pay a ransom, typically in cryptocurrency. Not all decryption keys work, so payment does not guarantee that the files will be recovered.
Security provider SonicWall reported nearly 500 million attacks through September 2021, with a staggering 1,748 attempted attacks per organization. This is equivalent to a business facing 9.7 ransomware attempts every day. (SonicWall)
The average ransom paid by mid-sized organizations was $170,404 while the average cost of resolving a ransomware attack was $1.85 million (Sophos)
3. Malware:
Malware is a catchall term for any malicious software, including worms, ransomware, spyware, and viruses. It is designed to cause harm to computers or networks by altering or deleting files, extracting sensitive data like passwords and account numbers, or sending malicious emails or traffic. Malware may be installed by an attacker who gains access to the network, but often, individuals unwittingly deploy malware on their devices or company network after clicking on a bad link or downloading an infected attachment.
In 2020, 61 percent of organizations experienced malware activity that spread from one employee to another. In 2021, that number rose to 74 percent, and in 2022, it hit 75 percent (Mimecast).
4. Data Breach:
A data breach occurs when the data for which your company/organisation is responsible suffers a security incident resulting in a breach of confidentiality, availability or integrity. (EU)
1,291 data breaches through September 2021. This number indicates a 17% increase in data breaches in comparison to breaches in 2020, which was 1,108. There is also a steep increase in the number of data compromise victims (281 million) during the first nine months of 2021 (ITRC)
The average total cost of a breach in 2021 was $4.24 million. (IBM)
5. DDOS
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
There were 9.84 million DDoS attacks in 2021. (HIPPA) The average cost of a DDoS attack in the US is around $218k without factoring in any ransomware costs (Corero)
Cybersecurity best practices:
With the move to hybrid and remote work, a security model needs to be adopted that protects people, devices, apps and data regardless of location. A Zero Trust framework starts with the principle that you can no longer trust an access request, even if it comes from inside the network. To mitigate your risk, assume you’ve been breached and explicitly verify all access requests. Employ least privilege access to give people access only to the resources they need and nothing more
Conduct regular cybersecurity training
Cybersecurity is a shared responsibility across the organisation. As shown by earlier statistics most attacks come from human error/inside the org. With personal and work devices used interchangeably, the risk is compounded. Regular training can help mitigate risk and prepare your employees in the event of an attack.
Institute cybersecurity processes
To reduce your risk from cyberattacks, develop processes that help you prevent, detect, and respond to an attack. Regularly patch software and hardware to reduce vulnerabilities and provide clear guidelines to your team, so they know what steps to take if you are attacked.
You can get guidance from cybersecurity frameworks such as the National Institute of Standards and Technology (NIST).
Invest in comprehensive solutions
As the risk to your business from cybersecurity increases, as does the technology solutions that help address security issues. I’ll address some of the Microsoft offerings below
Protect access to your resources with a complete identity and access management solution that connects your people to all their apps and devices. A good identity and access management solution helps ensure that people only have access to the data that they need and only if they need it. Capabilities like multifactor authentication help prevent a compromised account from gaining access to your network and apps.
Stay ahead of threats and automate your response with security information and event management (SIEM) and extended detection and response (XDR). A SIEM solution stitches together analytics from across all your security solutions to give you a holistic view into your environment. XDR protects your apps, identities, endpoints, and clouds, helping you eliminate coverage gaps.
Identify and manage sensitive data across your clouds, apps, and endpoints with information protection solutions that. Use these solutions to help you identify and classify sensitive information across your entire company, monitor access to this data, encrypt certain files, or block access if necessary.
Control access to cloud apps and resources and defend against evolving cybersecurity threats with cloud security. As more resources and services are hosted in the cloud, it’s important to make it easy for employees to get what they need without compromising security. A good cloud security solution will help you monitor and stop threats across a multicloud environment.
Microsoft Security products:
Azure Active Directory: Cloud Active directory. Secure adaptive access with a complete identity and access management solution.
Microsoft Sentinel: Birds-eye view across the enterprise with cloud-based SIEM and AI.
Microsoft 365 Defender: Prevent and detect attacks across your identities, endpoints, and apps with automation and AI.
Microsoft Defender for Cloud: Protect multicloud and hybrid cloud workloads with built in XDR capabilities
Microsoft Defender for Cloud Apps: Deep visibility of cloud apps with a leading cloud access security broker.
Microsoft Defender for Endpoint: Discover and defend Windows, macOS, Linux, Android, iOS and network devices against sophisticated threats.
Microsoft Defender for Identity: Protect on-premise identities and help detect suspicious activity with cloud intelligence.
Microsoft Defender for IoT: Full visibility and continuous threat monitoring of your IoT infrastructure.
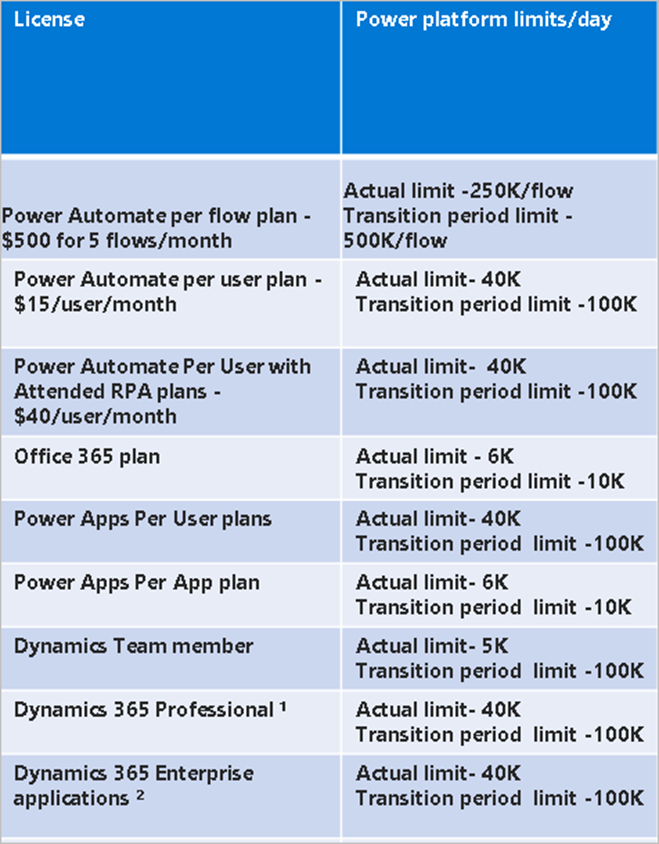
Did you know that since 2019 Microsoft have had a Power Platform daily usage limit per user in place? See Requests limits and allocations – Power Platform | Microsoft Docs
It is unlikely that you knew this as the limits have not been enforced, that is until now!! With the go live in May 2022 of Power Platform Request usage reporting in the Power Platform Admin Centre, Microsoft have now started the 6 month countdown to enforcement so impacts will be seen in late 2022. The result may mean ordering capacity add-ons for your high activity users.

Transition Period
Over the coming six month transition period, request limits will be higher than final enforcement limits.
|
Performance profile
|
Limits during transition period
|
Limits after transition period
|
|---|---|---|
|
Low
|
10,000
|
6000
|
|
Medium
|
100,000
|
40,000
|
|
High
|
500,000
|
250,000
|
Looking at the impacts on specific licence types the Dynamics Team Member users are certainly ones to look at closely as the limits during transition are set at 100K but drop to 5K on enforcement!!
Actions
During the transition period review and understand the reports now available in the Power Platform Admin Centre, analyse your data for trends and identify users who exceed the daily usage limitations.
Useful Microsoft Docs Resources:
Requests limits and allocations
Requests limits and allocations – Power Platform | Microsoft Docs
Transition period
Types of Power Automate licenses – Power Platform | Microsoft Docs
View detailed Power Platform request usage information in the Power Platform admin center (preview)
Requests limits and allocations – Power Platform | Microsoft Docs
What counts as Power Platform request?
Types of Power Automate licenses – Power Platform | Microsoft Docs
Frequently asked questions
Requests limits and allocations – Power Platform | Microsoft Docs
To discuss more on the Microsoft Power Platform please talk to your regular Micromail account manager or email our dedicated Microsoft Licensing Team on info@micromail.ie to organise a call.

Since 2017, Microsoft and Adobe have been working together to unite data, content, and processes for their customers. The strength and diversity of their global partner ecosystem is now more important than ever, as growing customer expectations for seamless customer experience have raised the bar on collaboration, integration and time to market.
In 2021, we are seeing a new wave of innovations to improve collaboration and business agility between the two, across all touchpoints.
In Micromail, we find ourselves in the unique position to be both Ireland’s leading Microsoft Licensing Solution Provider (LSP) and Ireland’s only Worldwide enabled Adobe Platinum Reseller with experts in both vendors. We would like to talk about some of these integrations so that you can get the most out of your investments.
Acrobat + Teams
Adobe Acrobat integration with Microsoft Teams allows you to effectively collaborate in real-time on PDF documents with other team members. Simply download the Acrobat app from your Teams app store and sign in to your Acrobat account. You can use the Adobe Acrobat app’s commenting features to write notes to yourself as you view or read documents. Or use the annotation tools like Insert Sticky Note, Highlight Text, or Draw markups on the PDF to share with your teammates.
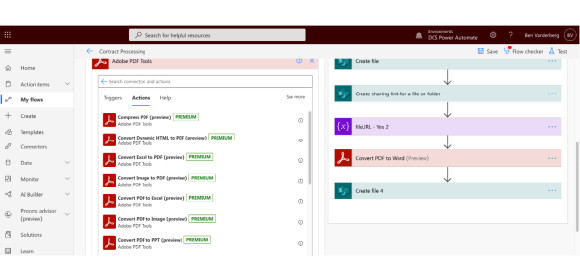
Acrobat + Power Automate
The Adobe PDF Tools Power Automate connector brings high-fidelity PDF manipulation capabilities to perform document actions such as create, export, combine, compress and protect PDF files. This new service provides additional flexibility for users who want to perform tasks like converting Word documents using optical character recognition (OCR), or securing, modifying, and exporting PDF documents as part of a custom document workflow – all within Power Automate.
Adobe and Azure SSO
Authenticate your users quickly using Open ID Connect (OIDC). You can also add Microsoft Azure AD Sync (Azure Sync) to the directories set up with Microsoft Azure to automate user management. Azure Sync automates the user management for your Admin Console directory. You can easily add Azure Sync to any federated directory in the Admin Console regardless of its identity provider (IdP). To use Azure Sync, you must have your organization’s users and groups data stored in the Microsoft Azure Active Directory (Azure AD).
Adobe Sign and….well, everything
Adobe Sign is Microsoft’s eSignature solution of choice, and comes with out of the box integration with the Office stack allowing users to send documents for signature directly from within Microsoft Word, Outlook, and PowerPoint. Adobe Sign is also the preferred e-signature solution across the Microsoft enterprise portfolio, including SharePoint, Dynamics,Teams, Flow, and PowerApps. Adobe Sign also allows users to Embed e-signature processes into your custom business applications and update data in back-end systems automatically with comprehensive APIs.
Adobe Sign + Teams
Getting things approved is part of almost evey workflow. And because more than 100 million users collaborate with co-workers in Teams, it makes sense to enable Adobe Sign e-Signature workflows right inside the Teams Approval interface. Start an approval flow with an e-signature in the same place you send a chat, in a channel conversation or from the Approvals app itself. It’s that easy!
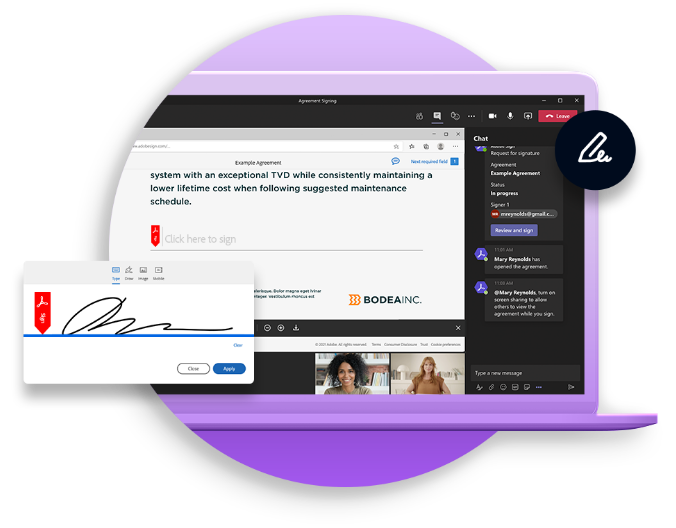
Most eSignature solutions deliver documents via email or weblink with little instruction or description. But some documents require a live conversation to ensure the signer feels comfortable. Other documents may legally require a live signing experience. Live Sign in Adobe Sign for Teams revolutionises the signing experience for both senders and signers by making a secure face-to-face signing a reality, without the need for anyone to travel. Senders can walk recipents through any document or agreement during a Teams video meeting. They can explain each page, answer questions, check for understanding and even read natural visual clues in real time. And recipents can then sign the document live durin the Teams meeting with legally binding e-Signatures.
Adobe Sign + Dynamics
Adobe Sign works natively with Microsoft Dynamics 365 so you can integrate it into your current Dynamics 365 document process with no coding required, and your staff can manage their entire eSignature workflow without ever leaving Dynamics 365. Documents can be sent to multiple recipents in any order that enables two or more recipients to receive the document simultaneously within a defined approval sequence. Your customers can sign documents fron any device, wherever they are.

Adobe Sign + Sharepoint
It is easy to set up Adobe Sign on your Sharepoint environment and from there, create clever workflows to speed up business processes. Take a look at the below example to see what Sign can do within Sharepoint.
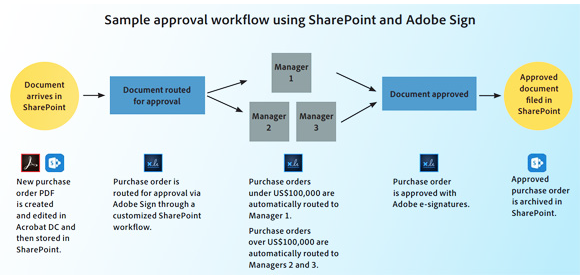
Further, you can create a folder within Sharepoint that collects all signed documents across the organisiation.
Adobe Sign + Power Automate
The Adobe Sign Power Automate connector provides a set of event triggers and actions that automatically start a signature process, kick off tasks after an agreement is signed, keep track of the signature status using notification templates and store signed agreement in your Microsoft environment and other applications. Many complex workflows require a large number of recipients, form fields and documents. The Adobe Power Automate connector includes a ‘support array’ feature that allows users to create robust workflows with Adobe Sign that contain dynamic form fields, recipients and documents in an intuitive and seamless way. Adobe Sign templates can be accessed from the Power Automate home page.
To discuss more on Adobe and Microsoft integrations please talk to your regular Micromail account manager or email our dedicated Adobe team on adobe@micromail.ie to organise a call.
I am very pleased to announce that Micromail has been selected as the exclusive supplier of Microsoft Azure in Ireland under the OCRE IaaS+ framework agreement. For the past 4 years Micromail has been a supplier of Microsoft Azure under the GEANT framework. OCRE is the successor to GEANT so we are very happy to continue to supply Azure and associated services to the Higher and Further Education community within Ireland for the next 4 years.
The HEAnet is Ireland’s National Research and Education Network (NREN) and HEAnet clients can avail of the OCRE framework.
OCRE Project Director David Heyns (GÉANT) said, “I am really excited by the opportunities this framework provides for the institutes, the NRENs, the European Open Science Cloud (EOSC), and the successful suppliers of these services. We look forward to showcasing the tremendous benefits that consumable commercial cloud-based services bring to the research and education community in Europe in terms of agility, flexibility and vastly improved outcomes.”
Micromail can offer the following to Higher and Further Education organisations as part of the OCRE framework:
- Discounted Azure consumption rates
- Expert licensing, billing, contractual and procurement advice from our dedicated Education team
- Azure Professional Services such as Migration, Modernisation of Applications and Cloud Management & Operations delivered by our parent company Ergo, current Microsoft Ireland Partner of the Year
- LinkedIn Learning at special pricing with Campus-wide licensing options giving access to a digital library of over 16,000 expert-led courses
- Micromail in association with Microsoft will be running a series of webinars for OCRE customers in the near future. Details to be published soon
To discuss more on Azure and the OCRE framework please talk to your regular Micromail account manager or email our dedicated Education team on info@micromail.ie to organise a call.

